What Is The Mac Name For The Windows Network Adapter
How to find the MAC address using the Settings app. To view the MAC address assigned to your Wi-Fi or Ethernet network adapter using the Settings app on Windows 10, do the following: Open Settings. Click on Network & Internet. Click on Wi-Fi (or Ethernet). Click on the network connection. Ethernet Adapter: If your server has more than one Ethernet adapter, select. If you are using a Mac OS X computer with more than one physical network adapter. To find your Host Name and Physical Address using the Windows Command.
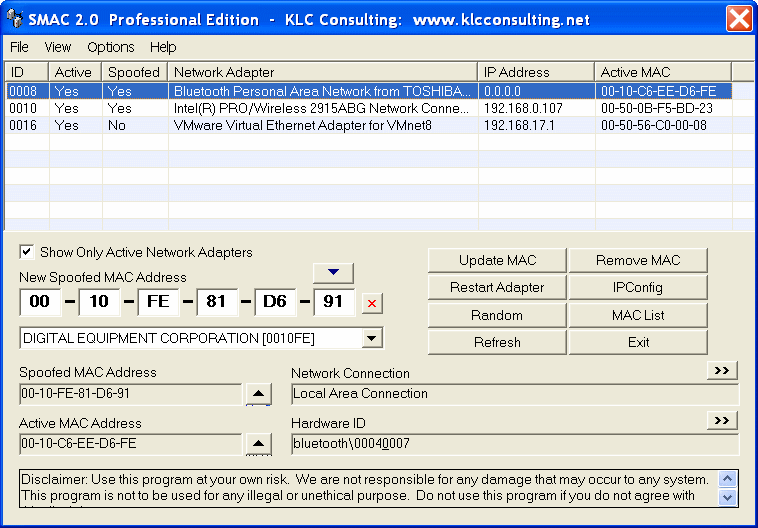
Each device that is integrated into a computer network requires a network adaptor. This adapter receives a worldwide unique identification number from the manufacturer: the MAC address. This enables devices like desktop computers, tablets, or mobile phones to be identified in the network and addressed as required. If a device has several network adapters (for example, for several LAN connections or different communication standards like Ethernet, WiFi, FDDI, Bluetooth, or Token Ring), a different address is available for each standard. Download os x yosemite for mac. Conflicting MAC addresses are a basic requirement for error-free network communication.
Data transmission in computer networks is a complex communication process in which different requirements including reliability, security, and efficiency must be met. This can be illustrated using the (abbreviation for open systems interconnection) – a reference model developed by the ISO (International Organization for Standardization) that maps network communication to 7 layers. During data transmission, each layer of the OSI model is run through on both the sender and receiver sides. MAC addresses are used on the backup layer (layer 2) of the OSI model – actually, the media access control sublayer introduced by the Institute of Electrical and Electronics Engineers (IEEE). The backup layer is located between the bit transfer layer (layer 1) and the switching layer (layer 3). While the bit transmission layer provides protocols and tools responsible for maintaining the physical connection, protocols on the backup layer control how different systems share the available transmission medium.
That's great for grandma, but for those of us who use Chrome all the time and know our way around the browser, it's a frustrating change.  (Maybe it's a way of trying to teach users to use the address bar instead of the search box -- but if so, shouldn't the search box go away once you get it?) Your synced tabs from other devices, meanwhile -- one of Chrome's coolest elements, particularly for those of us who use Android -- are now a step further away and hard to find. And on top of that, when you type something into the search box, it actually shows up in the address bar, anyway -- which just looks and feels odd. Once you realize you can search by typing into the address bar, after all, having a search box in the middle of the screen is redundant and a waste of space.
(Maybe it's a way of trying to teach users to use the address bar instead of the search box -- but if so, shouldn't the search box go away once you get it?) Your synced tabs from other devices, meanwhile -- one of Chrome's coolest elements, particularly for those of us who use Android -- are now a step further away and hard to find. And on top of that, when you type something into the search box, it actually shows up in the address bar, anyway -- which just looks and feels odd. Once you realize you can search by typing into the address bar, after all, having a search box in the middle of the screen is redundant and a waste of space.
Secure system connections are abstracted from the physical connection. The actual transmission of data packets takes place at the switching level via IP. For example, if you want to send an IP packet over Ethernet, your computer transmits a data frame that is addressed to the target computer’s MAC address on the backup layer, according to the OSI model. An Ethernet data frame contains information that is read out at different levels of the OSI model. Data frames in IPv4 networks contain the following components: • Destination address (destination computer MAC address) • Source address (sender’s MAC address) • Control information for data flow control • User data (the data packet that needs to be transmitted later on the switching layer) • Checksums that ensure data integrity A target computer that receives a data frame first reads it on the backup layer and compares the target address of the frame with its own MAC address.

If the addresses match, the target computer starts interpreting the frame at the next higher level. The bit sequence of each MAC address is divided into 4 areas, each of which encodes different information. • Bit 1 (receiver): The first bit of the MAC address specifies whether it is an individual or group address. This bit is called I/G (short for individual/group). If I/G = 0, it is a unicast address for a single network adapter. Multicast addresses are identified by I/G = 1 and are addressed to several receivers. • Bit 2 (registry): The second bit of the MAC address indicates whether it is an address with global validity (universal) or whether the address has been assigned locally (local).
The bit is called U/L. If U/L = 0, the address is valid worldwide as a universally administered address (UAA). Addresses that are only locally unique are called locally administered address (LAA) and are marked with U/L = 1. • Bit 3–24 (manufacturer identification): Bits 3 to 24 encode an identifier (organizationally unique identifier, OUI), which is assigned exclusively to hardware manufacturers. The assignment of OUIs is usually public and can be determined via databases. A corresponding service is available, for example, on.
• Bit 25-48 (network adapter identifier): Bits 25 to 48 provide device manufacturers with 24 bits for assigning a unique hardware identifier (organizationally unique address, OUA). This means that 2 24 (= 16.777.216) unique OUAs can be assigned per OUI.